Failure testing, Statistical control, Total quality management – There isn’t a dearth of approaches followed by Quality Assurance teams of organizations. No doubt, these approaches have proven their mettle as a fail-safe tool before delivering a solution or rendering a service to a client. But are they enough?
Innovation distinguishes between a leader and a follower. – Steve Jobs
At GreyB, our work involves interacting with inventors from around the globe. This makes us feel as if we are on an island surrounded by a sea of innovation. Hence, it’s innovation that runs through our veins. It’s an inseparable part of our DNA.
Thus, whenever we get a tough case, one thing that we least adopt is a traditional approach. Why? Because tough cases are tough as they cannot be solved through traditional approaches. They require lateral thinking which can only be introduced when you have few people whose job is to hack into the traditional way of solving the problem.
With that in mind, we developed our own methodology by innovating the way quality is taken care of. But how, you ask? Well, we developed a process we like to call Concept Hacking.
what does concept hacking mean?
Concept hacking is the hacking of thoughts/concepts prevailing in the mind of an analyst performing a patent search. In general, when a person conducts an in-depth research, he/she ignores the related, out of the box/tweaked areas of a concept.
It’s not intentional as our approaches get limited by the knowledge and experience that we have. Thus, no matter what is the length and breadth of your knowledge in a technological area, you may have no information of standpoint of thousands of different attorneys whose drafted patents you were studying in 100 different ways.
That’s where concept hacking comes into the picture.
A set of researchers are trained to watch how an analyst is conducting a project, such as an invalidity search, from an eagle’s eye and understand what’s going on in his/her head, like a computer hacker. The main aim is to target the critical point where researcher thinks that every possible area has been explored. It is at this moment when concept hackers come up with alternatives, if any, with minor clues to be explored next. They gather information regarding the plausible and unexpected areas.
When one of our clients got to know about this approach, he related concept hacking with the following anecdote:
In China, there is a special army called ‘The Blue Army which is employed to fight against its own native army. Seems strange? The blue army’s role is to give toughest of fights, hurdles, and challenges to their soldiers so that when they face real situations, they are all the more prepared to face anything.
Is Concept hacking a Client’s Need?
Yes. If you want to be the best.
Why?
Because your clients’ need results without regard to what methodology you use. Further, traditional approaches decrease your probability of finding results.
Let me elaborate.
The objective of concept hackers is to understand the psychology of an analyst while s/he conducts a project. Be it an invalidity search, infringement analysis or landscape analysis, a concept hacker stays in constant communication with the researcher, for that matter.
To make it more relatable, let me share an analogy.
The expression H(x) = αsin(w1x) + βcos(w2x) + γex, was the requirement for an invalidation search which involved trigonometric functions. The research team became aggressive to locate the prior art as such expressions are not an easy nut to crack.
First, the patent literature was explored minutely as there were high chances of having such an expression elaborated as a textual description in the specification of a patent. A lot of time was spent but to no avail.
In the next step, non-patent literature was explored. History repeated itself.
The researchers were about to run out of new strategies. Concept Hackers, in another area of the same office, however, were toiling to develop an analogy/ideology to figure out where else the concept could be searched and what the search team was missing.
After analyzing all the concepts related to the invention, the Concept Hackers found that a mathematical expression could also be present in the form of a circuit as trigonometric functions describe a circuit’s input and output behavior with a good approximation.
The research team, hence, was suggested checking various circuit diagrams dealing with sine, cosine signals, and the exponential signal which looked like a hit-and-try approach to them. However, they were open to any new idea that could lead to the relevant result. The Concept Hackers, on the other hand, were more confident about the strategy.
The search team once again started their hunt with full swing. After few hours on search, the team identified one circuit which was a relevant reference, describing two systems:
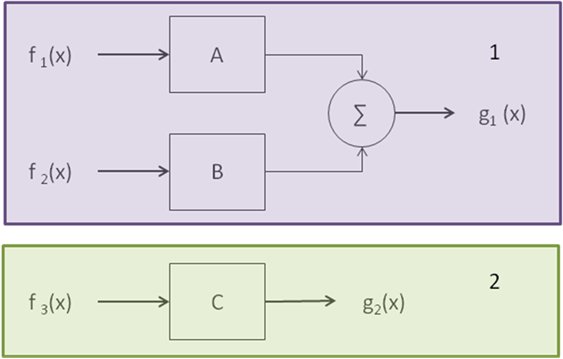
The first system employed two input signals f1(x) & f2(x) and provided one output signal g1(x). The second system employed one input signals and one output signal f3(x) & g2(x) respectively.
The identified reference, however, was not disclosing the formula or expression we needed explicitly. It, however, disclosed that the block A & B has sinusoidal outputs which lead us to the observation that g1(x) must be somewhat similar to Asinθ + Bcosθ.
Further, it was mentioned the block C can have an exponential output i.e. eθ. Everything was going on in an interesting direction. Both the hacking and research team were trying to figure how to combine system-1 and system-2 to get the desired output to knock out the patent.
We exclusively started analyzing backward and forward citations of the identified references, but it was of no use. Not the ones to give up, we continued searching. We came across a research paper of the inventor (of patented invention) describing a system which was combining the systems 1 & 2. Bang on, this was it!
The example above is one among many cases which gives you an idea of how a concept hacking team thinks and how powerful it can be.
With different researchers, different scenarios take place. Whatever the scenario, the concept hacker’s main job is to figure out the barrier holding back an analysts’ thought by understanding his psychology through his search logic.
Some may argue that a senior person guiding the researcher should identify the same. In that case, I would like to take the Blue Army example again. A Major should guide the soldiers under him in the best possible manner. But when does a soldier learn the most?
When he is in a real combat.
Authored By: Abhishek Bhatia, Team Leader, Concept Hacking